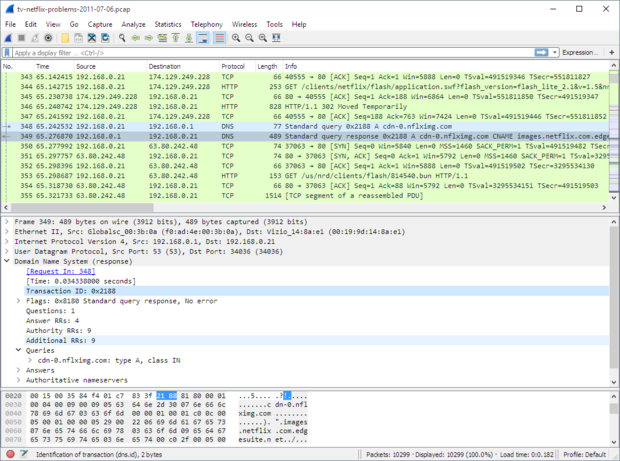
Hi all,I have a large number of devices at home, and when I installed pi-hole, I decided to let it handle DHCP so as to have more useful log entries - I get to see device names instead of just IP addresses. But, this morning there was a colossal fuckup and pihole stopped working. I googled a lot, and tried lots of things, but in the end, I had to teleport my pi and reinstall the whole system.Upon importing the setup, I discovered that none of my static leases had transferred. I'm going to have to do them all again, but I would prefer for this to be the last time. Is there a way to export the list of static DHCP leases? Some config file lurking somewhere that I can copy?Thanks.
The file /etc/dnsmasq.d/04-pihole-static-dhcp.conf contains your DHCP reservations. Don't bother with /etc/pihole/dhcp.leases as it is just a list of active DHCP leases, not the static ones.I have a large number of devices at home, and when I installed pi-hole, I decided to let it handle DHCP so as to have more useful log entries - I get to see device names instead of just IP addresses.You can also just use conditional forwarding to a different DHCP server (e.g.
Your router) if you don't want your Pi-hole to manage DHCP.
The Raspberry Pi can do a lot, especially now that the new Raspberry Pi comes with wireless capabilities already on board. It can take the place of a ton of different (and more expensive) devices – including a router! If you turn your Raspberry Pi into a wireless access point, you can make it act as a router. It’s not the most powerful thing in the world, but it does work, and the project is a lot of fun. How to use your Raspberry Pi as a wireless access pointWe’re going to get into the command line a bit here, but this project isn’t really all that difficult. All we’re really doing is using Raspbian and installing a couple packages that give the Pi the ability to do router-like things like assign IP addresses to devices that connect to it.
Step 1: Install and update RaspbianThen plug everything in and hop into the terminal and check for updates and ugrades: sudo apt-get updatesudo apt-get upgradeIf you get an upgrade, It’s a good idea to reboot with sudo reboot. Step 2: Install hostapd and dnsmasqThese are the two programs we’re going to use to make your Raspberry Pi into a wireless access point.
To get them, just type these lines into the terminal: sudo apt-get install hostapdsudo apt-get install dnsmasqBoth times, you’ll have to hit y to continue. Hostapd is the package that lets us create a wireless hotspot using a Raspberry Pi, and dnsmasq is an easy-to-use DHCP and DNS server.We’re going to edit the programs’ configuration files in a moment, so let’s turn the programs offbefore we start tinkering: sudo systemctl stop hostapdsudo systemctl stop dnsmasqStep 3: Configure a static IP for the wlan0 interfaceFor our purposes here, I’m assuming that we’re using the standard home network IP addresses, like 192.168.###.###. Given that assumption, let’s assign the IP address 192.168.0.10 to the wlan0interface by editing the dhcpcd configuration file.
Install Raspberry Pi
Start editing with this command: sudo nano /etc/dhcpcd.confNow that you’re in the file, add the following lines at the end: interface wlan0static ipaddress=192.168.0.10/24denyinterfaces eth0denyinterfaces wlan0(The last two lines are needed in order to make our bridge work –- but more on that inStep 8.)After that, press Ctrl+X, then Y, then Enter to save the file and exit the editor. Step 4: Configure the DHCP server (dnsmasq)We’re going to use dnsmasq as our DHCP server. The idea of a DHCP server is todynamically distribute network configuration parameters, such as IP addresses, forinterfaces and services.dnsmasq’s default configuration file contains a lot of unnecessary information, soit’s easier for us to start from scratch. Let’s rename the default configuration file andwrite a new one: sudo mv /etc/dnsmasq.conf /etc/dnsmasq.conf.origsudo nano /etc/dnsmasq.confYou’ll be editing a new file now, and with the old one renamed, this is the config file that dnsmasq will use. Type these lines into your new configuration file: interface=wlan0dhcp-range=192.168.0.11,192.168.0.30,255.255.255.0,24hThe lines we added mean that we’re going to provide IP addresses between 192.168.0.11 and 192.168.0.30 for the wlan0 interface. Step 5: Configure the access point host software (hostapd)Another config file! This time, we’re messing with the hostapd config file.
Open ‘er up: sudo nano /etc/hostapd/hostapd.confThis should create a brand new file. Type in this: interface=wlan0bridge=br0hwmode=gchannel=7wmmenabled=0macaddracl=0authalgs=1ignorebroadcastssid=0wpa=2wpakeymgmt=WPA-PSKwpapairwise=TKIPrsnpairwise=CCMPssid= NETWORKwpapassphrase= PASSWORDNote that where I have “NETWORK” and “PASSWORD,” you should come up with your own names. This is how you’ll join the Pi’s network from other devices.We still have to show the system the location of the configuration file: sudo nano /etc/default/hostapdIn this file, track down the line that says #DAEMONCONF=”” – delete that # and put the path to our config file in the quotes, so that it looks like this: DAEMONCONF='/etc/hostapd/hostapd.conf'The # keeps the line from being read as code, so you’re basically bringing this line to life here while giving it the right path to our config file. Step 6: Set up traffic forwardingThe idea here is that when you connect to your Pi, it will forward the traffic over your Ethernet cable.
So we’re going to have wlan0 forward via Ethernet cable to your modem. This involves editing yet another config file: sudo nano /etc/sysctl.confNow find this line: #net.ipv4.ipforward=1and delete the “#” – leaving the rest, so it just reads: net.ipv4.ipforward=1 Step 7: Add a new iptables ruleNext, we’re going to add IP masquerading for outbound traffic on eth0 using iptables: sudo iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADEand save the new iptables rule: sudo sh -c 'iptables-save /etc/iptables.ipv4.nat'To load the rule on boot, we need to edit the file /etc/rc.local and add the followingline just above the line exit 0: iptables-restore. Hello and thank you for the tutorial. It’s the only one working since updating to Stretch 🙂Now that I’ve replicated the tutorial, I’d like to implement a slightly different version of it. I’d like to use the Raspberry Pi 3 as an access point AND as a client simultaneously. This is for a little project I’m working on (building a weather station).
This should be possible with the Wi-Fi chipset built into the Raspi. There is no need for the clients that access the Raspi AP to have internet connectivity, so there’s no need for forwarding traffic (only the Raspi needs internet connectivity). I’m rather new to networking on Linux, so I don’t bring much experience to the table.
Unfortunately, there is no other way than this to realize the project. Can this be done by simply altering some of the above steps? What would be the right way of doing so? If not, could anyone give me some pointers to it?I have found some tutorials for doing so, but all of them work with /etc/network/interfaces. Unfortunately, editing anything in this file breaks access to wireless connectivity (“no wireless interface found”)Hopefully someone can help me.
Thanks in advance!Kind regards,Deki. Hi,First of all, thank you so much for this tutorial!! I tried several others and this is the only one that truly and easily worked!I’m having a little problem though. Other devices (like my smart TV for instance) can actually connect to my Raspberry, but when I use OpenVPN to connect my Raspberry to a NordVPN server, these devices don’t take advantage of the VPN.
I thought that when the Raspberry is using OpenVPN, any device that connects to it would connect to the VPN as well but it doesn’t seem to be as simple as that and I missing something here. Do you have any advice or tip to help me finish my little project? Well done!Thank you for helping me get this working. Tried multiple others and was glad to find one that works with Stretch!If I could suggest a mod, it would be calling out the aspects that drive bridge mode vs. Acting as a standalone AP/router.Ideally, I’m going for an AP that can also route traffic through the eth0 (if connected) but function independently if no Internet is available. After disabling the bridge/denyinterface parts, I’ve got the AP functioning in standalone mode, and the Pi can see the Internet, but Wi-Fi connected clients cannot.
Getting closer!. Adding a bridge after you configured DNS, DHCP and NAT masquerading seems to be incorrect.
These are two distinct configurations, after all.If you bridge eth0 and wlan0 together, these essentially become parts of the same subnet with Pi being completely transparent. In this case the DNS/DHCP functionality should be coming from the Ethernet, and the whole dnsmasq and iptables business is not needed.If, instead, you configure the Pi as a router, it becomes a proper host inbetween two separate subnets (one for eth0 and one for wlan0). In this case you do need dnsmasq and the iptables routing, however you should not bridge eth0 and wlan0. This tutorial skips the step of running “iptables-restore. The latest version of hostapd does not play well with wpasupplicant on Stretch. The simplest way to to fix this is to disable wpasupplicant on the wireless interfaces you want to run hostapd on. You can do this by adding the following line to to the relevant WLAN interface stanzas in /etc/dhcpcd.conf.nohook wpasupplicante.g.interface wlan0nohook wpasupplicantstatic ipaddress=192.168.0.1/24If you think about it it makes sense.
Wpasupplicant is a service to authenticate clients to access points. Hostapd is a service that runs the wireless interface as an access point that will receive authentication request from clients. Running both hostapd and wpasupplicant on an interface does not make any sense and only worked by accident in the past.